Learnings from the Industry Targeted Cyber Attack Statistics of 2025
This article analyzes cyber threat data from the year 2025 to highlight recurring attack patterns across the full spectrum of organizations, from large enterprises to small and medium-sized businesses (SMBs). Threat actors often reuse infrastructure such as IP addresses, domains, and malware variants across multiple campaigns. By studying historical indicators and tactics, security teams in every sector can uncover these overlaps, strengthen attribution, and proactively anticipate future attacks before they escalate.
TABLE OF CONTENTS
OBJECTIVES OF THE ANNUAL CYBER THREAT ANALYSIS
CYBER ATTACK LANDSCAPE 2025: CATEGORIES, PRIMARY OBJECTIVE, COMMON VECTORS, AND REPRESENTATIVE FAMILIES
USA Cyber Attack Trends of Year 2025
India Cyber Attack Trends of Year 2025
DIFFERENT TYPES OF CYBER ATTACKS OF 2025
RANSOMWARE LANDSCAPE 2025: TYPES, TACTICS, AND TARGETS
MALWARE LANDSCAPE 2025: TYPES, TACTICS, AND TARGETS
CYBER ATTACK TYPES AND THEIR PRIMARY TARGET IT ASSETS, COUNTRIES, AND BUSINESS DOMAINS
DEFINING THEMES THAT SHAPED 2025
NOTABLE FAMILIES, ACTORS, AND TACTICS OF 2025
Ransomware and Extortion
APTs and State-Aligned Activity
RATs, Backdoors, and Loaders
Infostealers and Keyloggers
Botnets and DDoS
Mobile, Spyware, and Stalkerware
Web App and Session Abuse
E-Commerce, Cloud, and Supply Chain
IMPACT PATTERNS AND AFFECTED SECTORS
STATE-SPONSORED CYBER ATTACK TRENDS
GLOBAL CYBERSECURITY SPENDING (DEFENSE AND OFFENSE) BY NATION – 2025 OUTLOOK
DEFENSIVE PRIORITIES FOR 2026
HOW CAN AN ORGANIZATION BE MORE CYBERSECURE AND CYBER-RESILIENT?
BDLSCCI Framework Benefits for SMBs/SMEs/MSMEs
OBJECTIVES OF THE ANNUAL CYBER THREAT ANALYSIS
This knowledge helps security teams uncover hidden patterns, strengthen attribution, and anticipate future threats more effectively. It also enables better prioritization of risks, refinement of defensive strategies, and preparation for regulatory and compliance requirements, while supporting awareness programs that build resilience across the workforce. In essence, annual trend analysis transforms past incidents into a predictive lens, empowering organizations to proactively adapt and safeguard against the next wave of cyber attacks.
Studying annual cyber attack trends provides business owners and C-level executives with a strategic lens to understand the evolving threat landscape and make informed decisions that protect both operations and reputation. By reviewing historical data, leaders can see which attack types, such as ransomware, phishing, or supply chain breaches, caused the greatest disruption and financial loss, and which industries were most frequently targeted. This insight allows them to prioritize investments, allocate budgets effectively, and strengthen resilience planning for business continuity. It also highlights compliance gaps and regulatory risks, enabling executives to prepare for audits and avoid penalties. Most importantly, trend analysis transforms cybersecurity from a purely technical issue into a boardroom priority, empowering decision makers to align security strategies with overall business goals, build trust with customers and partners, and maintain a competitive edge in an increasingly hostile digital environment.
For more updates on Cyber News and related insights, SecureClaw invites you to follow our official LinkedIn page: SecureClaw Cyber Threat Advisory.
^ GO BACK TO TABLE OF CONTENTS ^
CYBER ATTACK LANDSCAPE 2025: CATEGORIES, PRIMARY OBJECTIVE, COMMON VECTORS, AND REPRESENTATIVE FAMILIES
Figure 1: 2025's Domainwise Cyberattacks on Industries Worldwide Report Prepared by SecureClaw
The Cyber Attack Landscape 2025, shown in Figure 1, provides a structured overview of how modern threats are categorized, what drives them, and the techniques they employ. It highlights distinct attack categories such as ransomware, phishing, supply chain compromise, and nation‑state espionage. Each category is mapped to its primary objective - whether financial gain, data theft, disruption, or surveillance. The illustration also outlines common attack vectors, including email, malicious links, compromised credentials, and vulnerable software, demonstrating how adversaries infiltrate systems. Finally, it connects these elements to representative malware families or campaigns, offering concrete examples that make the abstract threat landscape more tangible and easier to understand.
^ GO BACK TO TABLE OF CONTENTS ^
USA Cyber Attack Trends of Year 2025
Figure 2: USA Cyber Attack Trends of Year 2025
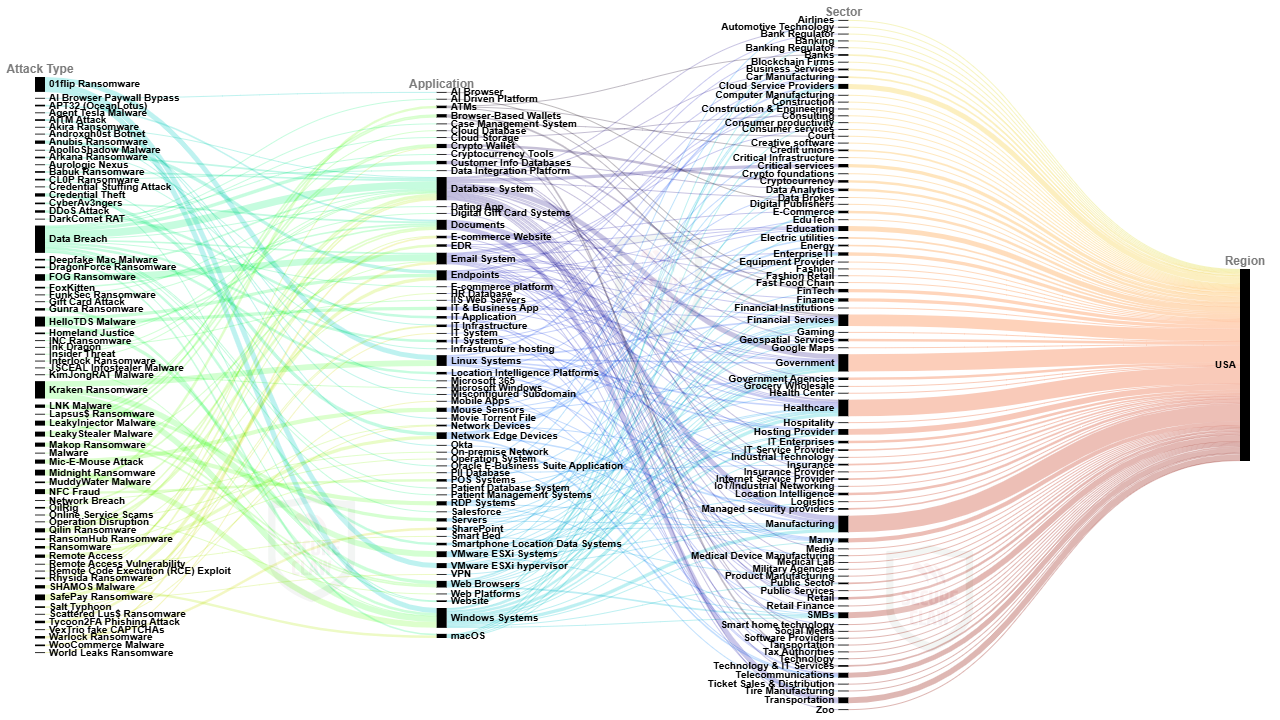
As shown in Figure 2, in year 2025, organizations across the USA faced a surge of diverse and sophisticated cyberattacks ranging from ransomware strains like 01flip, Akira, Babuk, CL0P, DragonForce, FunkSec, Kraken, Lapsus$, Midnight, Qilin, RansomHub, Rhysida, Scattered Lus$, Warlock, and World Leaks to advanced malware families such as Agent Tesla, ApolloShadow, HelloTDS, JSCEAL Infostealer, KimJongRAT, LeakyInjector, LeakyStealer, SHAMOS, and WooCommerce malware. Threat actors leveraged botnets (Androxgh0st), RATs (DarkComet), and APT groups (APT32/OceanLotus, MuddyWater, OilRig, FoxKitten) to infiltrate networks, while new-age exploits like AI browser paywall bypass, AiTM attacks, deepfake Mac malware, and VexTrio fake CAPTCHAs highlighted the growing role of AI in cybercrime. Traditional attack vectors such as credential stuffing, credential theft, insider threats, DDoS attacks, data breaches, NFC fraud, gift card scams, and remote code execution exploits continued to plague enterprises, alongside politically motivated campaigns like CyberAv3ngers, Homeland Justice, and Operation Disruption. Collectively, these incidents underscored the escalating complexity of the U.S. cyber threat landscape, where financial extortion, espionage, fraud, and disruption converged to challenge organizational resilience and national security.
^ GO BACK TO TABLE OF CONTENTS ^
India Cyber Attack Trends of Year 2025
Figure 3: India Cyber Attack Trends of Year 2025
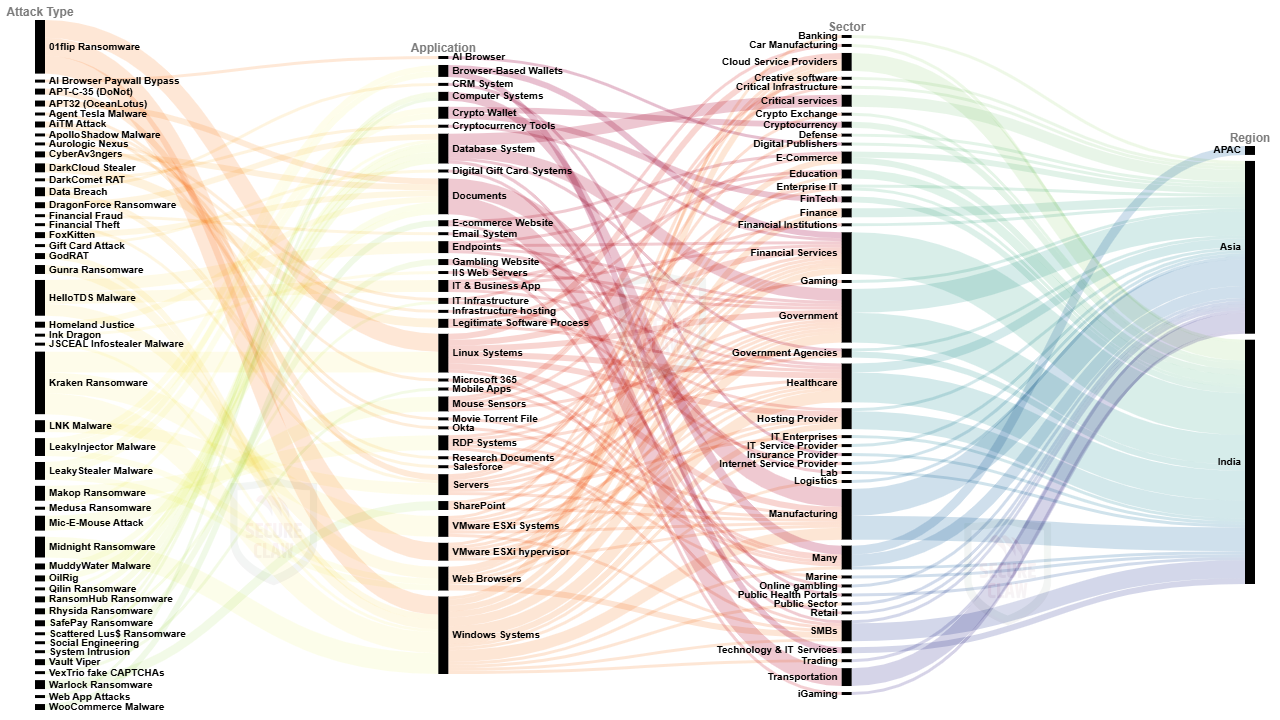
As shown in Figure 3, in year 2025, Indian industries were heavily targeted by a wide spectrum of cyberattacks that blended ransomware campaigns such as 01flip, DragonForce, Gunra, Kraken, Makop, Medusa, Midnight, Qilin, RansomHub, Rhysida, SafePay, Scattered Lus$, Warlock with stealer and malware families like Agent Tesla, ApolloShadow, DarkCloud Stealer, HelloTDS, JSCEAL Infostealer, LeakyInjector, LeakyStealer, LNK malware, Vault Viper, WooCommerce malware, and GodRAT. Advanced persistent threat groups including APT32 (OceanLotus), APT-C-35 (DoNot), MuddyWater, OilRig, and FoxKitten conducted espionage and disruption operations, while politically motivated collectives such as CyberAv3ngers, Homeland Justice, and Ink Dragon added to the threat landscape. Attackers exploited AI-driven techniques like AI browser paywall bypass, AiTM attacks, and VexTrio fake CAPTCHAs, alongside traditional vectors such as data breaches, financial fraud and theft, gift card scams, social engineering, system intrusions, and web application attacks. Remote access tools like DarkComet RAT further enabled persistence and surveillance. Collectively, these incidents revealed the growing convergence of financial crime, espionage, and disruptive operations in India’s cyber ecosystem, underscoring the urgent need for resilience, regulatory compliance, and proactive defense across critical sectors.
^ GO BACK TO TABLE OF CONTENTS ^
The table below highlights insights of widely reported across global cyber news sources.
| Category |
Primary Objectives |
Common Vectors |
Representative Families/Actors |
| Ransomware |
Disruption, Extortion
|
Phishing, RDP, Vulnerabilities
|
LockBit, CL0P, Black Basta, Rhysida, Akira, RansomHub, Medusa, SafePay, World Leaks, DragonForce, 8Base, Babuk, Qilin, Warlock, Blue Locker, Albabat, Arkana, CyberVolk
|
| Credential & Access Theft |
Account Takeover, Lateral Movement
|
Phishing, Infostealers, Password Managers
|
T1555.003 Password Stealer, Credential Stuffing, ACRStealer, Lumma, DarkCloud, Poseidon, Chihuahua, Snake Keylogger, XLoader, Infostealers
|
| Remote Code Execution & Critical Vulnerabilities |
Initial Foothold, Privilege Escalation
|
Web RCE, OS Command Injection, SQLi
|
Remote Code Execution (RCE) Exploit/Vulnerability, OS Command Injection, SQL Injection, Browser Cache Smuggling, Agent session smuggling
|
| Botnets & DDoS |
Disruption, Monetization
|
IoT/routers, L7/L3 attacks
|
L7 DDoS botnet, XorDDoS, MikroTik Botnet, PumaBot, GorillaBot, VOIP-based Telnet botnet
|
| APT & Espionage |
Long-term Access, Data Exfiltration
|
Spear-phish, Supply Chain, RATs
|
Lazarus, OilRig, MuddyWater, Bitter, APT32/OceanLotus, APT37, MirrorFace, Void Blizzard, Salt Typhoon, FoxKitten, Homeland Justice
|
| RAT/Backdoors |
Persistence, C2 control
|
Droppers, Loaders, Malvertising
|
SystemBC, Remcos (Backdoor/RAT), DarkComet, MysterySnail, Neptune RAT, Big Shark RAT, Silver RAT, ScoringMathTea RAT, GodRAT, UNC5174 RAT
|
| Financial Fraud & Scams |
Monetization, Theft
|
Phishing, Vishing, Fake Personas
|
Financial Theft/Fraud, Online Service Scams, Gift Card Attack, Vishing, Tycoon2FA phishing, AI browser paywall bypass
|
| Supply Chain & Web App |
Scale-out Compromise
|
NPM/PyPI, CI/CD, Plugins
|
Supply Chain Attack, WooCommerce Malware, Androxgh0st Botnet, Website Impersonation, Web App Attacks
|
| Mobile & Spyware |
Surveillance, Credential Theft
|
Mobile Exploits, Stalkerware
|
Pegasus, SpyMax, FlexiSPY, Gorilla Android malware, Landfall spyware, Exploiting mobile vulnerability
|
| Blockchain & ICS |
DeFi Theft, Physical Impact
|
Smart Contracts, ICS Protocols
|
Smart contract exploitation, Blockchain smart contract vulnerability, Hijacking fleets of inverters, Satellite communication disruption
|
^ GO BACK TO TABLE OF CONTENTS ^
DIFFERENT TYPES OF CYBER ATTACKS OF 2025
As illustrated in Figure 4, numerous variants of malware, ransomware, and other cyber threats were reported across global cyber attack news sources during 2025.
Figure 4: Quarterly Summary of Different Types of Cyber Attacks of 2025
^ GO BACK TO TABLE OF CONTENTS ^
RANSOMWARE LANDSCAPE 2025: TYPES, TACTICS, AND TARGETS
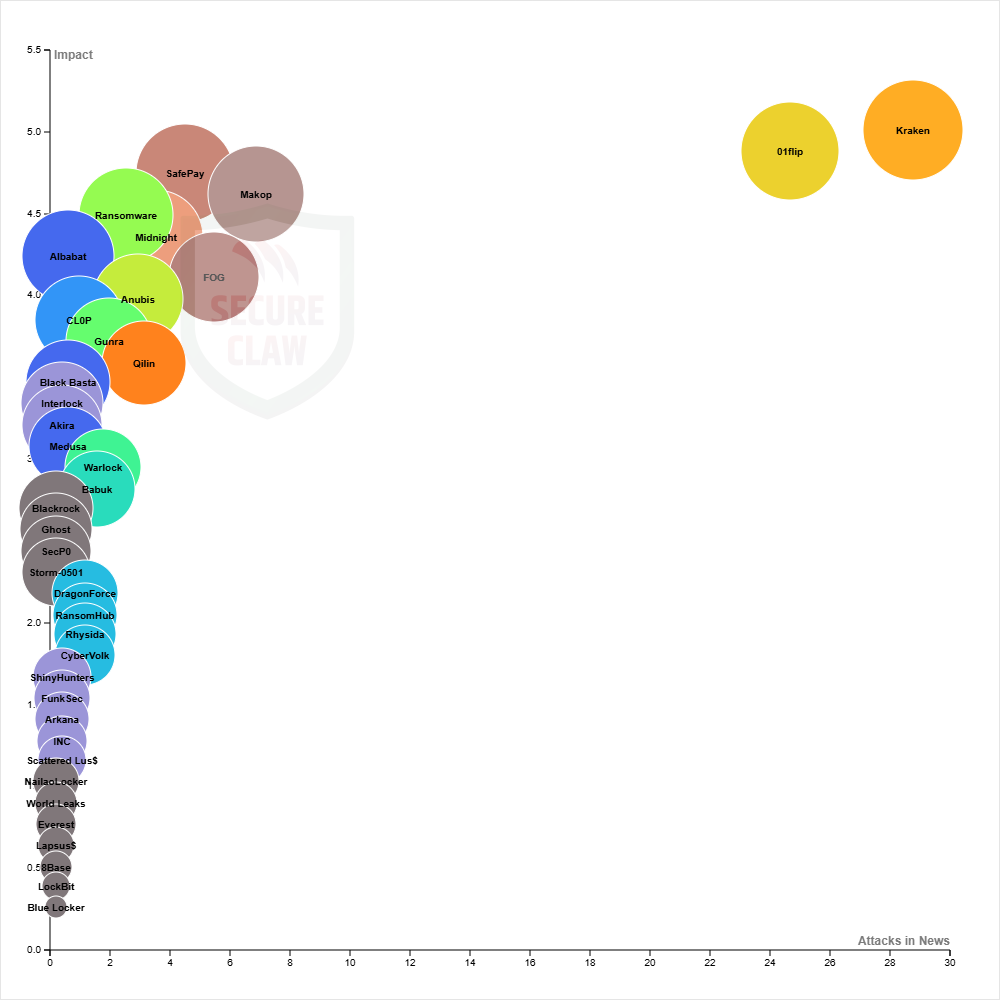
The figure 5 illustrates the proportion of ransomware cyber attacks reported in the news relative to their average impact, taking into account the targeted IT assets, the number of affected countries, and the business domains attacked in 2025, as documented by multiple news sources. The table below highlights several ransomwares that were widely reported across global cyber news sources.
Figure 5: Reported ransomware attacks versus average impact on IT assets, countries, and business domains in 2025 (news sources)
| Ransomware Family |
Tactics |
Impact / Target Sectors |
| CL0P, LockBit, Black Basta, 8Base |
Multi‑extortion, rapid exploitation of zero‑days, data leaks
|
Cross‑sector outages, regulatory exposure, supply chain compromise
|
| Akira, Rhysida, RansomHub, Medusa, Qilin |
Double‑extortion, negotiation playbooks, tailored ransom demands
|
Acute downtime in healthcare, education, and local government
|
| Babuk, Makop, Everest, Midnight, NailaoLocker |
Encryption‑focused, mid‑tier ransomware, opportunistic targeting
|
SMBs, legacy systems, limited IR maturity exploited
|
| DragonForce, SafePay, World Leaks, FunkSec, Warlock |
Sector‑specific lures, regional targeting, localized campaigns
|
Regional businesses, e‑commerce, localized disruption
|
| Albabat, Anubis, Arkana, Ghost, Gunra, INC, Interlock, Kraken |
Emerging/lesser‑known variants, opportunistic attacks
|
Mixed impact, often targeting SMBs and poorly segmented networks
|
| Blue Locker, CyberVolk, FOG, SecP0 |
Niche/extortion‑style ransomware, smaller campaigns
|
Localized data leaks, reputational damage
|
| Blackrock, Scattered Lus$, ShinyHunters, Lapsus$, Storm‑0501 |
Data theft + extortion, breach‑driven ransomware hybrids
|
Credential leaks, insider recruitment, reputational exposure
|
^ GO BACK TO TABLE OF CONTENTS ^
MALWARE LANDSCAPE 2025: TYPES, TACTICS, AND TARGETS
The figure 6 illustrates the proportion of known malware cyber attacks reported in the news relative to their average impact, taking into account the targeted IT assets, the number of affected countries, and the business domains attacked in 2025, as documented by multiple news sources. The table below highlights several ransomwares that were widely reported across global cyber news sources.
Figure 6: Reported malware attacks versus average impact on IT assets, countries, and business domains in 2025 (news sources)
The table below highlights several malware variants that were widely reported across global cyber news sources.
| Malware Family |
Type / Tactics |
Impact / Target Sectors |
| ACRStealer, Infostealer, LeakyStealer, GammaSteel, XLoader |
Infostealers – browser/session theft, credential harvesting, MFA bypass
|
Credential stuffing, account takeover, fraud in finance & e‑commerce
|
| Snake Keylogger, InvisibleFerret, LeakyInjector |
Keyloggers – capture keystrokes, steal tokens
|
Identity theft, insider compromise, phishing amplification
|
| DanaBot, Sturnus Banking, FireScam |
Banking Trojans – inject into browsers, steal payment data
|
Financial fraud, e‑commerce theft, DeFi wallet compromise
|
| APT37, MuddyWater, Billbug, TAG‑110 |
APT/state‑aligned malware – espionage, supply chain pivots
|
Government, telecom, defense, regional influence operations
|
| KimJongRAT, KorPlug, MysterySnail RAT, Silver RAT, RokRat, ApolloShadow |
RATs/backdoors – persistence, modular C2, proxying
|
Long‑term espionage, data exfiltration, enterprise infiltration
|
| BPFDoor, NGate, HollowQuill, GhostSocks |
Backdoors/proxy malware – stealth tunneling, covert persistence
|
Enterprise networks, cloud environments, stealthy lateral movement
|
| ModiLoader, Gootloader, Matchboil & Dragstare, KeyPlug |
Loaders – deliver secondary payloads, modular infection
|
Enable ransomware/infostealer deployment, expand attack chains
|
| Raspberry Robin, Xred, Zhong, HelloTDS |
Worms/loaders – USB/network propagation, exploit chains
|
Rapid spread across SMBs, supply chain compromise
|
| MikroTik Botnet, XorDDoS, Proxyware |
Botnets/DDoS – application‑layer floods, misconfig exploitation
|
Telecom, energy, cloud services, VOIP disruption
|
| Gorilla Android, Deepfake Mac Malware, macOS Malware |
Mobile/OS malware – surveillance, privilege escalation
|
Exploits gaps in MDM, enterprise BYOD risks, data exfiltration
|
| WooCommerce Malware, SHAMOS |
Web/e‑commerce malware – formjacking, credential capture
|
Payment fraud, plugin trust erosion, supply chain risk
|
^ GO BACK TO TABLE OF CONTENTS ^
CYBER ATTACK TYPES AND THEIR PRIMARY TARGET IT ASSETS, COUNTRIES, AND BUSINESS DOMAINS
As illustrated in Figure 7, multiple IT assets were targeted by cyber attacks during 2025, according to reports from cyber attack news sources.
Figure 7: Cyber Attack Types and Their Primary Target IT Asset
As illustrated in Figure 8, top 14 countries/regions which were targeted by cyber attacks during 2025, according to reports from cyber attack news sources.
Countries where industries face the highest levels of cyber threats include the United States (approximately 16%), Europe (6%), India (around 5.32%), the United Kingdom (5.00%), Germany (5.00%), Canada (4.41%), Japan (4.22%), France (3.96%), Asia (3.76%), South Korea (3.63%), Africa (1.69%), the Middle East (1.62%), and Turkey (1.43%). In addition to these, numerous other nations report significant cyberattacks across their industries. These include China, Brazil, Egypt, Australia, Kenya, Serbia, Tanzania, Slovenia, Greece, Bosnia and Herzegovina, Singapore, Montenegro, Albania, North Macedonia, Croatia, Romania, Bulgaria, Rwanda, Kosovo, Taiwan, Iran, Italy, Switzerland, Belgium, Vietnam, Russia, Pakistan, the Philippines, Morocco, Iraq, Hong Kong, Ukraine, Mexico, Peru, Thailand, Colombia, Sweden, Denmark, Myanmar, Malaysia, Israel, Azerbaijan, the United Arab Emirates, Kuwait, Dubai, Poland, Mongolia, Austria, the Netherlands, and Indonesia, among others.
Many industries fail to report cyber threats, either despite existing compliance requirements or due to the absence of strict regulatory obligations in their countries. Consequently, only a limited number of cases are reflected in media reports.
Figure 8: Cyber Attack Types and Their Primary Target Countries
As illustrated in Figure 9, top 10 business domains which were targeted by cyber attacks during 2025, according to reports from cyber attack news sources.
In 2025, reports on cyberattacks reveal that government organizations remain the most heavily targeted sector, accounting for 24% of incidents. Healthcare follows closely at approximately 21%, while financial services represent 15%. Manufacturing industries face 11% of attacks, education 5%, and hosting providers, small and medium businesses (SMBs), and cloud service providers each account for about 2%. Beyond these primary targets, a wide range of other industries are also under persistent threat. These include telecommunications, transportation, enterprise IT, cryptocurrency, e-commerce, critical services, retail, the public sector, data analytics, construction, location intelligence, financial institutions, geospatial services, consumer productivity, fintech, critical infrastructure, smart home technology, IoT and industrial networking, blockchain firms, crypto foundations, energy, military, internet service providers, managed security providers, technology and IT services, defense, airlines, and electric utilities. Collectively, this broad spectrum of vulnerable domains underscores the pervasive and far-reaching nature of cyber threats across both public and private sectors.
Increased cyberattacks on government entities signify growing vulnerabilities in national infrastructure, heightened geopolitical tensions, and the urgent need for stronger cybersecurity frameworks. Also, since there are industry-specific cyberattack trends, the BDSLCCI framework can play an important role in securing the supply chain.
Figure 9: Cyber Attack Types and Their Primary Target Business Domains
^ GO BACK TO TABLE OF CONTENTS ^
DEFINING THEMES THAT SHAPED 2025
- AI-scaled social engineering:
Phishing and vishing leveraged generative content, voice cloning, and adaptive lure strategies, boosting click-throughs and bypassing traditional awareness training.
- Exploit-to-ransom pipelines:
RCE and web app weaknesses fed turnkey ransomware operations, shrinking dwell time and increasing multi-extortion pressure on backups and reputations.
- Infostealer economy:
Commodity stealers fueled credential stuffing and session hijack, enabling rapid lateral movement and persistent business email compromise loops.
- Botnet diversification:
Router/IoT-targeting botnets and L7 DDoS assaults impacted availability for SMBs and telecoms, with VOIP and API edges increasingly abused.
- Supply chain fragility:
Plugin ecosystems, CI/CD secrets, and dependency confusion widened reach, hitting e-commerce, SaaS, and MSPs.
- Mobile and privacy erosion: Spyware and jailbreak chains expanded surveillance risk; privacy compliance gaps magnified legal exposure across regions.
^ GO BACK TO TABLE OF CONTENTS ^
NOTABLE FAMILIES, ACTORS, AND TACTICS OF 2025
Ransomware and Extortion:
- In 2025, ransomware remained the most disruptive threat category, with families such as LockBit, CL0P, and Black Basta employing multi-extortion tactics, combining encryption with data leaks and rapid exploitation of zero-day vulnerabilities.
- These campaigns caused cross-sector outages and heightened regulatory exposure. Groups like Akira, Rhysida, RansomHub, Medusa, and 8Base refined double-extortion techniques, using targeted negotiation playbooks that inflicted acute downtime on healthcare, education, and local government institutions.
- Sector-specific variants such as DragonForce, SafePay, and World Leaks demonstrated tailored lures and regional targeting, underscoring how ransomware operators increasingly customize attacks to maximize impact.
^ GO BACK TO TABLE OF CONTENTS ^
APTs and State-Aligned Activity:
- Advanced Persistent Threats (APTs) such as Lazarus, OilRig, MuddyWater, Bitter, APT32, APT37, MirrorFace, Void Blizzard, and Salt Typhoon pursued objectives ranging from espionage and financial theft to regional influence.
- Their tradecraft relied on spear-phishing, supply chain pivots, and bespoke RATs, enabling long-term infiltration and covert data exfiltration.
- These campaigns highlighted the geopolitical dimension of cyber threats, where nation-state actors blend technical sophistication with strategic intent.
^ GO BACK TO TABLE OF CONTENTS ^
RATs, Backdoors, and Loaders:
- Remote Access Trojans and backdoors—including SystemBC, Remcos, DarkComet, MysterySnail, Neptune RAT, Big Shark, Silver RAT, GodRAT, and UNC5174—were widely deployed to maintain persistence, proxy traffic, and enable modular command-and-control.
- Loader ecosystems such as RokRat, KeyPlug, ModiLoader, and Paper Werewolf facilitated delivery of secondary payloads, reinforcing the layered nature of modern intrusion campaigns.
^ GO BACK TO TABLE OF CONTENTS ^
Infostealers and Keyloggers:
- Families like Lumma, DarkCloud, ACRStealer, Poseidon, XLoader, Snake Keylogger, and Chihuahua focused on browser and session theft, often bypassing multi-factor authentication through push fatigue and token abuse.
- These tools fed credential stuffing attacks and enabled rapid lateral movement across enterprise networks.
^ GO BACK TO TABLE OF CONTENTS ^
Botnets and DDoS:
- Botnet activity surged with XorDDoS, MikroTik Botnet, PumaBot, GorillaBot, L7 botnets, and VOIP-Telnet botnets orchestrating application-layer floods, API exhaustion, and VOIP disruption.
- Amplification via misconfigurations expanded their reach, threatening availability across telecom and cloud services.
^ GO BACK TO TABLE OF CONTENTS ^
Mobile, Spyware, and Stalkerware:
- Mobile surveillance tools such as Pegasus, SpyMax, FlexiSPY, Gorilla Android, and Landfall posed risks of surveillance, exfiltration, and privilege escalation.
- Enterprise device hygiene gaps and weak mobile device management (MDM) policies were frequently exploited, exposing sensitive personal and corporate data.
^ GO BACK TO TABLE OF CONTENTS ^
Web App and Session Abuse:
- Exploits including Remote Code Execution, SQL Injection, OS Command Injection, Browser Cache Smuggling, and Agent Session Smuggling enabled token theft, privilege escalation, and shadow administrator creation.
- These attacks reinforced the need for secure coding practices and robust web application firewalls.
^ GO BACK TO TABLE OF CONTENTS ^
E-Commerce, Cloud, and Supply Chain:
- Threats such as WooCommerce malware and the Androxgh0st botnet targeted online commerce and cloud ecosystems through formjacking, credential capture, and exploitation of misconfigurations.
- Plugin and update trust erosion highlighted the fragility of supply chains and the risks of third-party dependencies.
^ GO BACK TO TABLE OF CONTENTS ^
IMPACT PATTERNS AND AFFECTED SECTORS
- The healthcare and education sectors suffered data leaks and downtime from mid-tier ransomware, with legacy systems and flat networks amplifying the blast radius.
- Finance and e-commerce faced payment fraud, credential stuffing, and Magecart-style skimming, while smart contract exploits drained decentralized finance (DeFi) treasuries.
- Energy, telecom, and industrial sectors were hit by botnet-driven DDoS, inverter fleet hijacking, and satellite communication disruptions, exposing weak segmentation in critical infrastructure.
- SMBs and MSPs emerged as vulnerable pivot points in supply chain attacks, with limited incident response maturity and backup integrity exploited for broad contagion.
^ GO BACK TO TABLE OF CONTENTS ^
STATE-SPONSORED CYBER ATTACK TRENDS
As shown in Figure 10, several state-sponsored cyberattacks were highlighted in news coverage throughout 2025.
Figure 10: State-sponsored Cyber Attack Trends observed in News of 2025
State-sponsored hacking refers to cyberattacks conducted or supported by national governments as part of cyber espionage or warfare. Unlike ordinary cybercriminals seeking quick profit, these actors - often called Advanced Persistent Threats (APTs) - use sophisticated tools such as custom malware and zero-day exploits to infiltrate networks, maintain long-term access, and steal sensitive data or disrupt systems for strategic advantage. Their operations resemble professional espionage, remaining clandestine and undetected to maximize intelligence gains. APTs are “advanced” because of their tailored malware and stealthy techniques, “persistent” because they maintain long-term footholds, and a “threat” because of the serious damage they can cause.
State-sponsored hackers operate like professional spies rather than ordinary cybercriminals. Instead of seeking ransom, they infiltrate networks quietly, exfiltrating sensitive data such as defense blueprints while remaining undetected. Their goal is not publicity or profit, but long-term intelligence and strategic advantage.
In 2025, state-sponsored cyber operations escalated sharply across the globe, encompassing espionage, ransomware, disruptive attacks, and financial theft. Russia emerged as one of the most aggressive actors, launching campaigns such as ApolloShadow, GammaSteel, Matchboil, Raspberry Robin, and TAG-110 to penetrate embassies, defense systems, and NATO-linked organizations. In parallel, Russian-aligned ransomware groups - including Babuk, Rhysida, CL0P, Black Basta, LockBit, and Storm-0501 - targeted hospitals, police departments, and critical infrastructure. These activities blurred the boundary between cybercrime and state-directed hybrid warfare, underscoring Moscow’s reliance on digital tools to destabilize adversaries and extend influence beyond traditional battlefields.
China expanded its cyber espionage footprint through groups like Billbug, BPFDoor, KeyPlug, KorPlug, MysterySnail, NANOREMOTE, Silver RAT, Zhong, and ZnDoor. Their operations targeted certificate authorities, telecom providers, medical institutions, and multinational enterprises. By exploiting trusted infrastructure and cloud platforms, Chinese actors secured long-term access to sensitive data, reinforcing Beijing’s strategic focus on surveillance, intellectual property theft, and geopolitical intelligence gathering.
North Korea pursued both espionage and financial objectives. Groups such as APT37 (ScarCruft), RokRat, KimJongRAT, InvisibleFerret, and NimDoor macOS malware attacked South Korea, Japan, NGOs, and cryptocurrency exchanges. These campaigns enabled Pyongyang to bypass sanctions and finance its regime through unprecedented digital asset theft.
Iran continued disruptive operations via MuddyWater and APT34/OilRig, targeting Middle Eastern governments, telecoms, and Gulf oil sectors. These efforts combined espionage with sabotage, reflecting Tehran’s ambition to assert regional influence. Hamas-linked AshTag also surfaced as a notable actor, conducting espionage against Israeli and Middle Eastern institutions, highlighting the role of militant groups in state-aligned cyber warfare.
Other nations demonstrated offensive capabilities as well. The United States undertook proactive measures to dismantle foreign botnets and ransomware infrastructure, reinforcing its defensive posture while sustaining legacy disruption campaigns. Canada’s CSE engaged in espionage against foreign adversaries, while Pakistan’s Transparent Tribe (APT36) targeted Indian government, defense, and education sectors. India’s Operation Sindoor revealed its growing vulnerability to foreign campaigns, with large-scale attacks on government portals, power grids, and telecom networks.
The global spread of cyber warfare was further evident in campaigns by Vietnam’s OceanLotus (APT32), which targeted Chinese and Southeast Asian governments; Turkey’s StrongPity and Sea Turtle, which infiltrated European and Middle Eastern telecoms; and Israel’s Unit 8200, which conducted surveillance against regional adversaries and Palestinian groups. The UK’s GCHQ and NCSC ran counter-espionage operations against Russian APTs, while Saudi cyber units focused on Iranian-linked groups. Japan deployed state-backed RATs to counter Chinese espionage, and German and Polish NATO cyber units strengthened collective defense against Russian activity.
Together, these campaigns illustrate how cyber warfare has become a universal instrument of statecraft. Nations across all regions now leverage malware, ransomware, and advanced persistent threats to pursue strategic objectives. The convergence of espionage, disruption, and financial theft in 2025 highlights the growing complexity of the global threat landscape, with critical infrastructure, healthcare, defense, and digital finance remaining prime targets of state-sponsored operations.
The following reference links correspond to the cyber threats outlined in Figure 10.
^ GO BACK TO TABLE OF CONTENTS ^
GLOBAL CYBERSECURITY SPENDING (DEFENSE AND OFFENSE) BY NATION – 2025 OUTLOOK
While many countries do not explicitly disclose their investments in cyber operations, an analysis of various publicly available reports indicates that global cybersecurity spending (defense and offense) exceeds $212 billion in 2025, with state-sponsored operations accounting for a significant share.
The table below highlights several investments made by different countries and regions in 2025.
| Country |
Cyber Ops Investment (Approx, 2025) |
Focus Areas |
Notes |
| United States |
$10–12B annually |
Botnet takedowns, ransomware disruption, Indo-Pacific Command |
DoD Cyber Command + DOJ press releases; $1B explicitly for offensive ops |
| China |
$8–10B annually |
AI weaponization, espionage, supply chain infiltration |
PLA cyber units; heavy focus on global espionage |
| Russia |
$3–4B annually |
APT groups, hybrid warfare, ransomware |
Supports Gamaredon, Sandworm, LockBit-linked ops despite sanctions |
| United Kingdom |
£1–1.5B annually |
APT disruption, resilience, NATO cyber defense |
GCHQ/NCSC budgets; framed as resilience/disruption |
| Germany / Poland (NATO) |
$500M–1B annually |
Countering Russian APTs, NATO defense integration |
NATO CCDCOE reports; joint cyber forces |
| Japan |
$500M–800M annually |
China-linked espionage, RAT development |
JPCERT & NTT Security advisories |
| Saudi Arabia |
$300M–600M annually |
Targeting Iranian-linked groups, regional adversaries |
Recorded Future Middle East report |
| Iran |
$200M–400M annually |
Regional espionage, MuddyWater, APT34 |
Focus on adversaries and critical infrastructure |
| Israel |
$1–2B annually |
Advanced offensive ops, Stuxnet-style tools |
Strong private-public integration; legacy offensive capabilities |
^ GO BACK TO TABLE OF CONTENTS ^
DEFENSIVE PRIORITIES FOR 2026
- Organizations must adopt an identity-first approach, deploying phishing-resistant MFA, conditional access, session anomaly detection, and passkey rollouts while hardening SSO lifetimes.
- Exploit reduction requires continuous patching of RCE and critical vulnerabilities, WAFs with virtual patching, and code-to-cloud SBOM with secret scanning.
- Ransomware readiness depends on 3-2-1 backups with immutable storage, segmented recovery networks, and tabletop exercises for communication and regulatory response.
- Strengthening email and browser controls through DMARC/DKIM/SPF enforcement, sandboxing, and password manager policies is essential.
- Endpoint and network visibility should leverage EDR, memory detection, eBPF/NetFlow telemetry, and DNS/TLS inspection balanced with privacy.
- To counter botnets and DDoS, organizations need Anycast/CDN shielding, L7 rate limiting, VOIP protections, and IoT firmware governance.
- Mobile and privacy defenses must include MDM hardening, jailbreak detection, minimal-permission policies, and compliance gap mapping.
- Finally, supply chain assurance requires vendor risk scoring, plugin signing verification, CI/CD guardrails, least-privilege tokens, and periodic dependency attestation.
^ GO BACK TO TABLE OF CONTENTS ^
HOW CAN AN ORGANIZATION BE MORE CYBERSECURE AND CYBER-RESILIENT?
Below are a few recommendations for the organizations to improve their cybersecurity posture.
- Adopt a Defense-in-Depth Mechanism:
As more sophisticated cyber attacks have increased in many industry segments, just a couple of cybersecurity controls will not help. Organizations need to identify their mission-critical assets and need to adopt cybersecurity for various layers like data, application, host or endpoint, network, and physical perimeter, and then the overall governance cybersecurity layer.
There are many cybersecurity standards and frameworks available in the market helping in the structured implementation of the controls. American NIST and ISO 27001 (ISMS) are more popular in the world. Also, it is important to understand that 90% of the business population, which are small and medium businesses (SMBs), globally contribute to maximum employment and high value in GDP. In countries like India, SMBs are known as Micro, Small, and Medium Enterprises (MSMEs). In few countries these organizations also known as small and medium enterprises (SMEs). To reduce the cyberattack surface, these organizations can even adopt the Business Domain-Specific Least Cybersecurity Controls Implementation (BDSLCCI) framework, which is cost-effective, easy, and tailored to their business domain.
- Cybersecurity Awareness Training for Employees:
Cyberattacks often stem from inadequate employee cybersecurity awareness. Effective training should cover phishing precautions, policies, and insider threats, with employee testing for effectiveness.
- Beware of Supply Chain Attacks:
Third-party users, access to vendors and external applications should be monitored.
- Monitor Your Network:
Regularly monitoring network logs and business transaction notifications is crucial for detecting malicious activities and taking necessary action to prevent them.
- Regular Security Audits:
It is important to perform vulnerability assessment and penetration testing (VAPT) for the various IT assets of the organization, which should be part of the governance process, with processes enhanced as needed and compliance improved.
- Incident Handing Process is Must:
Organizations need to be ready with a working plan for the unseen cyber incident. They need to track incidents as a report until permanent closure. Also, organizations need to prepare a business continuity plan (BCP) for any unseen circumstances, including natural disasters and cybercrimes.
- Learn about Incident Reporting Process:
In the United States, under the Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA), covered entities must report cyber incidents to the Cybersecurity and Infrastructure Security Agency (CISA) within 72 hours. Additionally, ransom payments must be reported within 24 hours.
For healthcare organizations in the USA, under the Health Insurance Portability and Accountability Act (HIPAA), healthcare entities must report breaches involving personal health information within 60 days. For the banking sector of the USA, the Federal Deposit Insurance Corporation (FDIC) requires banking organizations to report significant cyber incidents within 36 hours.
As per the European Union, the General Data Protection Regulation (GDPR) requires organizations to report data breaches to the relevant supervisory authority within 72 hours.
In Australia, critical infrastructure entities must report cyber incidents within 72 hours under the Security of Critical Infrastructure (SOCI) Act.
The Indian Computer Emergency Response Team (CERT-In), a part of the Ministry of Electronics and Information Technology, has issued new guidelines under section 70B of the Information Technology Act, 2000, requiring all cybersecurity incidents to be reported within six hours of noticing or being informed about them. These guidelines are part of an effort to enhance the country's cybersecurity posture and ensure timely responses to potential threats.
Hence it is important to check where your organization is operating and the requirement of incident reporting according to the law of the land.
^ GO BACK TO TABLE OF CONTENTS ^
BDLSCCI Framework Benefits for SMBs/SMEs/MSMEs
SecureClaw is a venture of Dr. Pawar, which is on the mission of cybersecuring small and medium companies worldwide, which are known as MSMEs, small and medium businesses (SMBs), or even small and medium enterprises (SMEs), depending on their size, revenue, and location. For this article, let us consider the word SMB, which represents any of these kinds of companies. With his decades of international experience and research studies during his doctorate from the Swiss School of Business and Management in Geneva, Switzerland, Dr. Pawar has invented a new cybersecurity framework popularly known as Business Domain Specific Least Cybersecurity Controls Implementation (BDSLCCI), which is more focused on these kinds of organizations. Apart from continuous research and enhancement in BDSLCCI to make it more beneficial to MSMEs, SecureClaw also provides various cybersecurity services, which include the Virtual Chief Information Security Officer (V-CISO), Source Code Security Review, which is popularly known as static application security testing (SAST), dynamic application security testing (DAST), or vulnerability assessment and penetration testing (VAPT), as a few of its key offerings. These organizations have diverse experience in programming, telecom, and cybersecurity, which makes their expertise unique while designing solutions for their customers.
Cybersecurity is right for every business, regardless of its size, location, or revenue! The BDSLCCI Cybersecurity Framework complies with the maximum cybersecurity controls's categories using a tailored list of controls, especially useful for micro, small, and medium enterprises known as SMEs, SMBs, MSMEs, or startup companies.
by Dr. Shekhar A Pawar
Latest BDSLCCI Framework 3.0 has modified Defense in Depth (DiD) as well as Mission Critical Asset (MCA).
Visit www.BDSLCCI.com today to know more features and benefits!
If your organization is located in India, please visit www.BDSLCCI.in today to know more!
During international research studies by Dr. Pawar, the top management of SMB companies from 19 different countries participated.
It was evident that there were three major problems faced by those companies.
- Small and medium-sized companies are not having enough funds or allocated budget for the implementation of hundreds of controls mandated by existing cybersecurity standards.
- These companies do not have skilled teammates or other resources to implement and maintain cybersecurity controls.
- Top management is not able to see the return on investment (RoI) for cybersecurity implementation, as the top priorities of such companies are not directly aligned with the recommended controls by existing cybersecurity standards or frameworks.
Dr. Pawar's research reveals that each SMB has a unique business domain and mission-critical asset (MCA) based on their sector. MCAs, such as data, information, or infrastructure, are crucial for a SMB's core business. For instance, healthcare MCAs might be Electronic Medical Record (EMR) software, while banking, financial services, and insurance (BSFI) MCAs might be financial records. MCAs can be information-related or even business function-related.
Only antivirus or firewall kinds of cybersecurity controls are not enough to prevent cyber threats like ransomware. To protect an organization from sophisticated cyberattacks, it's important to implement defense in depth.
by Dr. Shekhar A Pawar
As shown in Figure 11, BDSLCCI's defense-in-depth strategy helps in reducing the risk of ransomware attacks.
Figure 11: BDSLCCI Framework's Defense in Depth (DiD) helping to lower the risk of a Ransomware Attack
MCAs weigh confidentiality, integrity, and availability differently, and SMBs need cybersecurity controls. Defense in Depth (DiD) strategy addresses people, process, and technology. BDSLCCI framework provides recommendations for implementing DiD controls in parallel with MCA, designed by Dr. Pawar.
There are multiple ways to get BDSLCCI certification.
- SMB can self-assist by directly registering itself on the BDSLCCI web portal. The BDSLCCI web portal provides secured access to various data points and guidance provided by the logic of the BDSLCCI framework.
- SMB can identify a BDSLCCI member company, which is a certification body of BDSLCCI, authorized to provide BDSLCCI certificates as one of its services.
- SMB can even hire BDSLCCI-authorized freelancers who can assist them in their BDSLCCI certification journey, where the final audit will be done by SecureClaw and the BDSLCCI certification and transcript will be issued by SecureClaw.
The BDSLCCI offers certifications and assessments at three different levels. On the incremental order of control implementation, SMB can be more cybersecure while reaching BDSLCCI Level 3.
Any startup, even one employee company, or any medium-scale company with hundreds of employees can get a customized or tailored cybersecurity controls list using BDSLCCI. It offers an ascending order of controls, aiding top management in decision-making. In situations where organizations need to take the Data Privacy and Protection Acts of their nation seriously to avoid high penalties if a data breach happens, or even to avail of cyber insurance, or to simply have better confidence in their way of working and handling customers’ critical assets, selecting SecureClaw’s BDSLCCI will be a very good choice. SecureClaw has been deployed in many SMBs/ SMEs/ MSMEs and has received good market feedback.
^ GO BACK TO TABLE OF CONTENTS ^
Hope this article will help many organizations to understand the importance of cybersecurity controls implementation to protect their business, reputation, finance, and growth in the new year.
You can also check this: Learnings from the Industry Targeted Cyber Attack Statistics of 2024